Active Defense and Hacking Back
22 Oct 2025This week, I joined a roundtable discussion on Active Defense - a topic I’ve explored before and even wrote a paper about back in 2016. It’s been some time since I revisited it, so I decided to spend a couple of hours mapping out my current mental model and sharing my thoughts publicly.
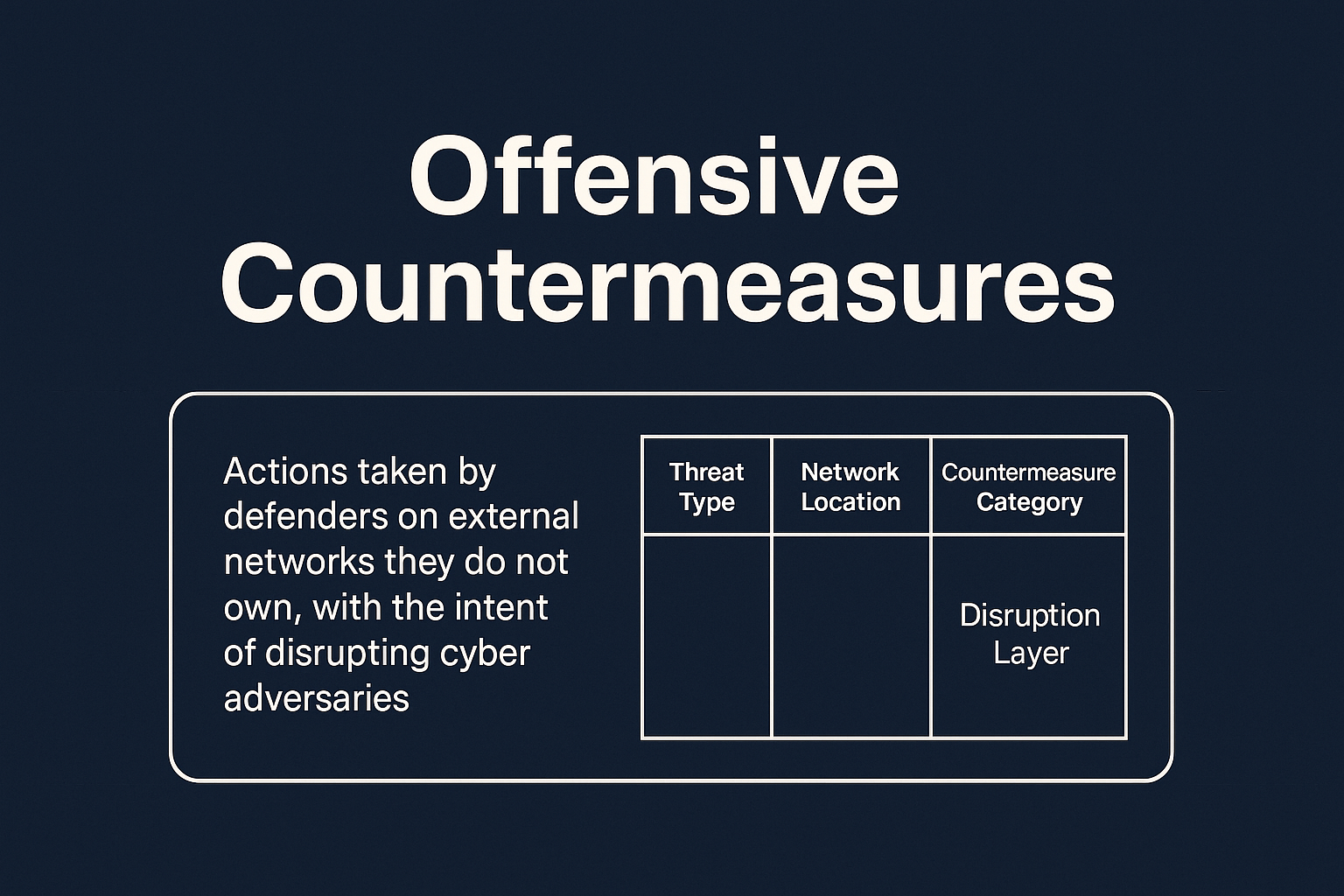
To begin with, I’ve never liked the terms Active Defense or Defend Forward. I prefer the term Offensive Countermeasures, which I believe more accurately captures what our industry is really trying to achieve.
Here’s how I define it:
Offensive Countermeasures are actions taken by defenders on external networks they do not own, with the intent of disrupting cyber adversaries.
In my model, I make four key distinctions to explain how it works:
- Threat Type
- Network Location
- Countermeasure Category
- Disruption Layer
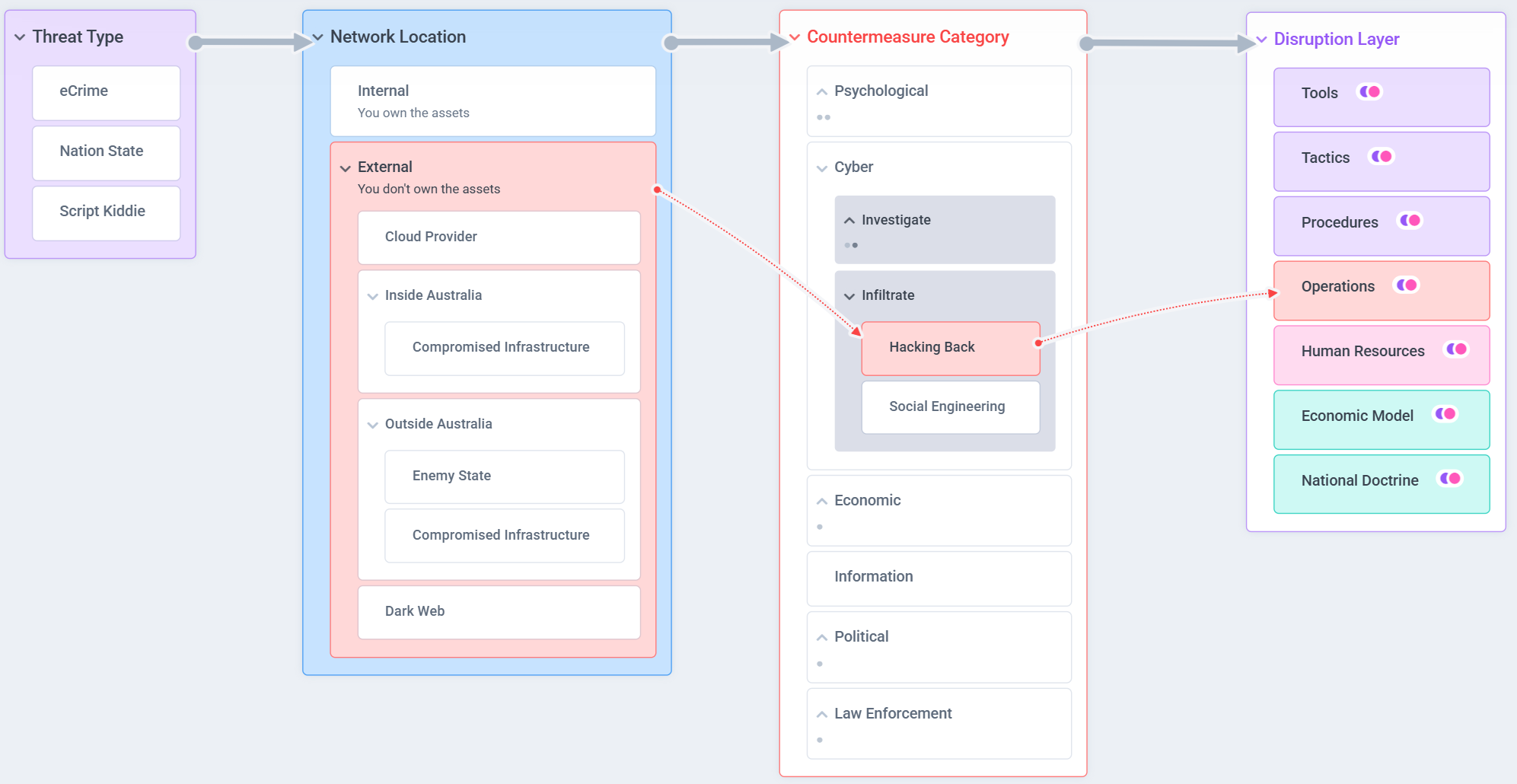
The details in image above are incomplete, but enough is presented to illustrate several key ideas.
First, it’s important to acknowledge that the industry, government, and military are already employing Offensive Countermeasures in practice. For example, when we take down a malicious domain, we are acting beyond our own network boundaries to disrupt one of the adversary’s tools.
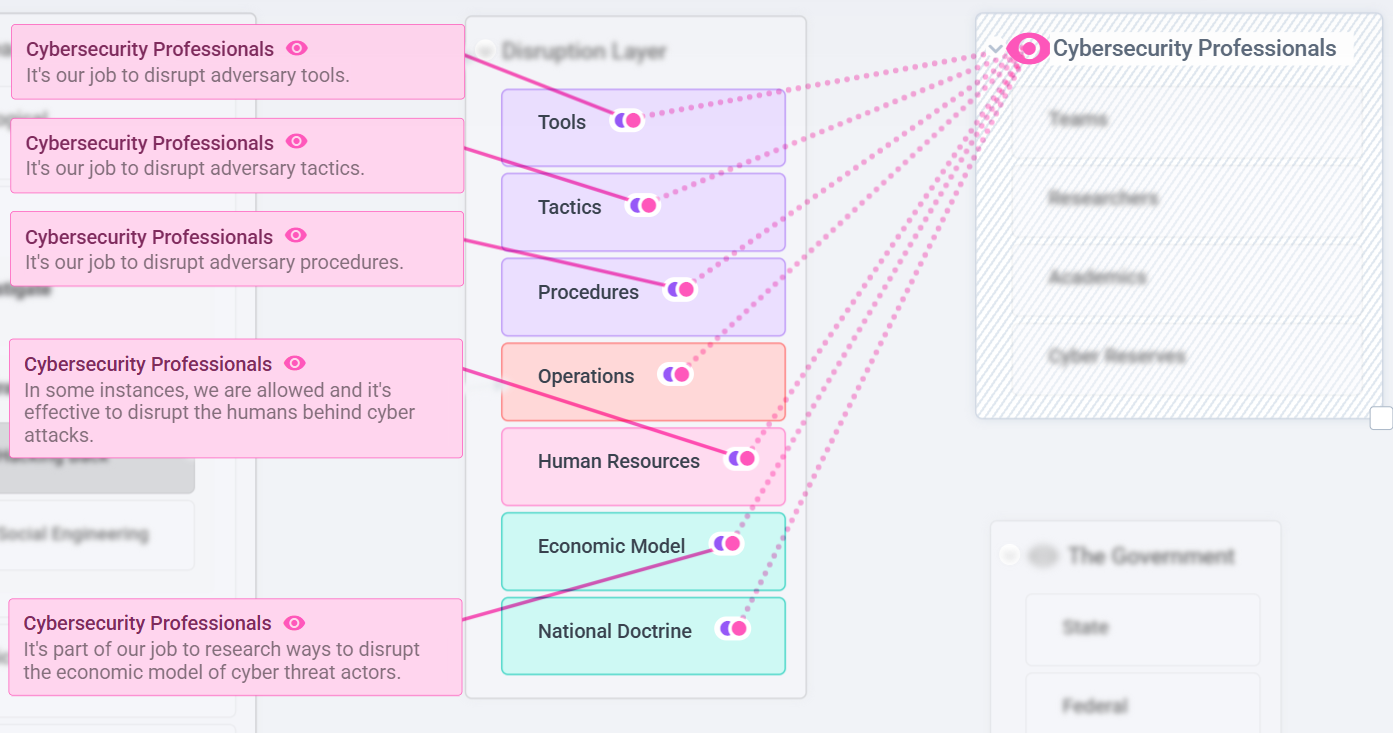
In fact, cyber professionals are not only permitted but expected to identify and execute actions that disrupt adversary tools, tactics, procedures, and even their underlying economic or human resource layers when legally and ethically justified.
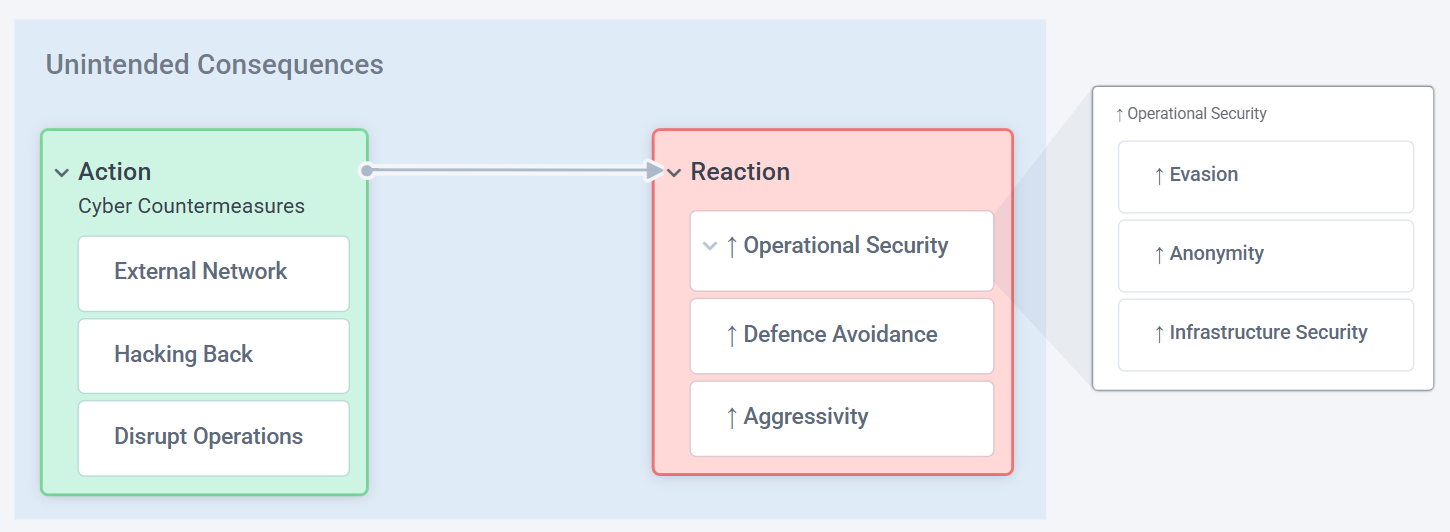
Second, the one action that consistently raises concern around Offensive Countermeasures is hacking back. The fear is that such actions could lead to unintended consequences - for example, prompting adversaries to harden their operational security, making them more difficult for law enforcement to track or disrupt in the future.
There’s also the fear of escalation. A hacked adversary may retaliate with greater aggression or adopt more destructive tactics, ultimately worsening the threat landscape rather than improving it.
Third, let’s set hacking back aside for a moment and treat it as the one scenario where perspectives will likely never fully align. Instead, let’s turn our attention to the broader spectrum of Offensive Countermeasure categories:
- Psychological: Undermining an attacker’s morale to discourage or halt further activity.
- Cyber: Disrupting the attacker’s tools, tactics, and procedures.
- Economic: Eliminating or constraining the attacker’s sources of funding.
- Information: Infiltrating adversary groups to dismantle them from within.
- Political: Using diplomacy to establish agreements with nations that host cyber adversaries and strengthen international cyber laws.
- Law Enforcement: Pursuing, arresting, and prosecuting adversaries through legal channels.
Each of these categories could warrant a full paper in itself. For now, I’m keeping the definitions concise to focus on conveying the core ideas.
If these categories sound familiar and you find yourself thinking, “We’re already doing all of this,” you’d be absolutely right. That wasn’t nearly as true back in 2016 - the field has advanced considerably since then.
Where we still have significant room for improvement, however, is in the coordination of these offensive countermeasures across all the different agents involved.
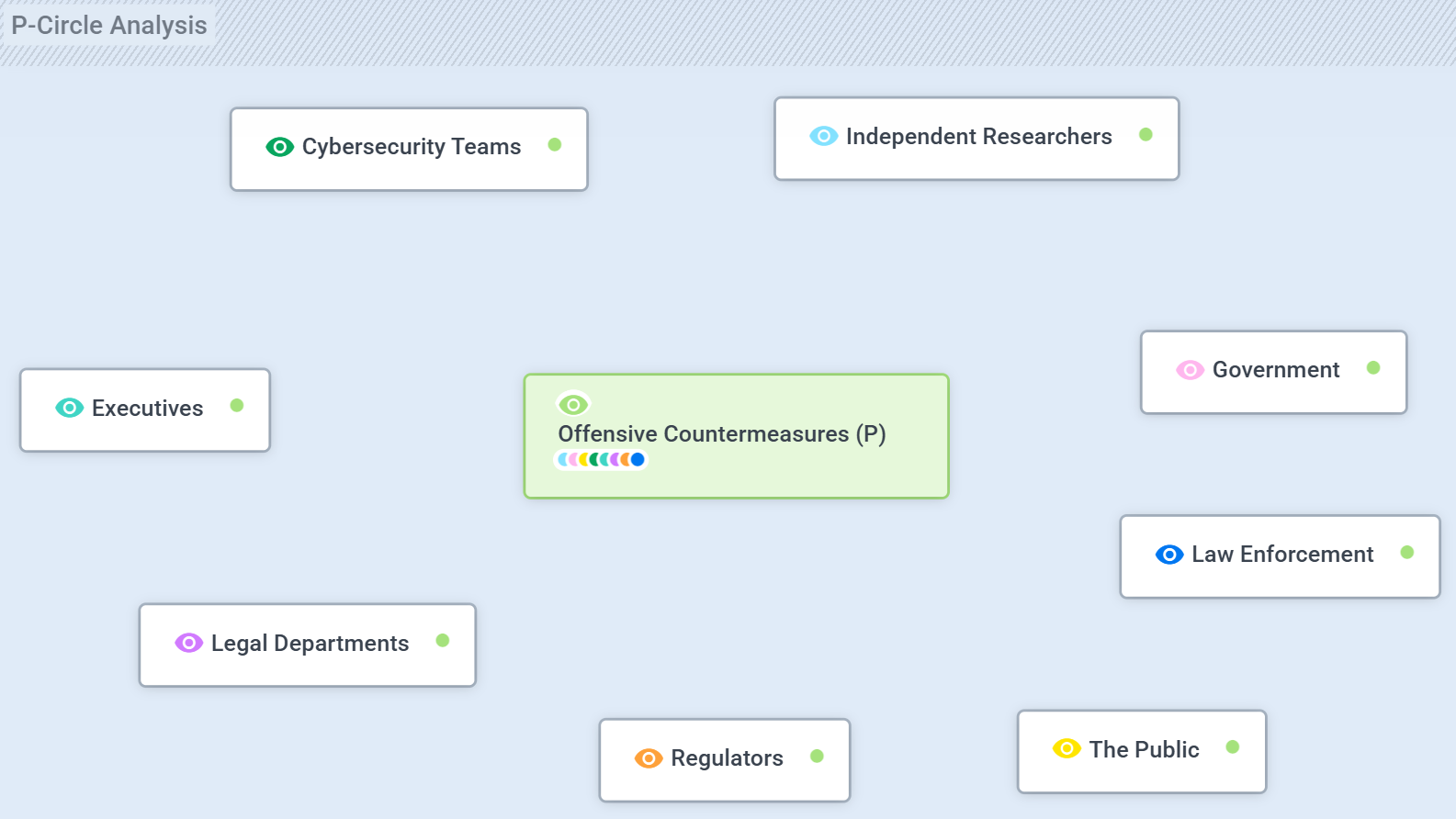
With that in mind, let’s now turn to a Perspective Circle Analysis:
-
Cybersecurity Teams view offensive countermeasures as a means to protect their organizations and contain the impact of major incidents.
-
Independent Researchers see offensive countermeasures as a way to contribute to national defense and disrupt threat actors independently. They publish malware analyses, create and share detection rules, and often investigate adversary infrastructure or campaigns on their own initiative.
-
Law Enforcement approaches offensive countermeasures with greater operational freedom but heightened caution. From their perspective, uncoordinated hacking back could interfere with ongoing investigations or compromise evidence collection.
-
Business Executives perceive offensive countermeasures through the lens of risk and responsibility. In crisis situations, they may face decisions about whether to authorize such actions and would benefit from a formal decision-making framework to guide lawful, proportionate responses.
-
Legal Practitioners focus on defining the boundaries of what is permissible. Their perspective centers on ensuring that all actions - whether by private organizations or government entities - are executed within the law, enabling them to provide sound advice to executives and cybersecurity teams.
-
Regulators see offensive countermeasures as a domain requiring clear governance. They aim to establish formal rules of engagement and educate both the private sector and the legal community on how to apply these responsibly.
-
Government Authorities view themselves as the coordinating body responsible for policy leadership. Their role is to set national guidelines, align efforts across all stakeholders, and ensure that offensive countermeasures serve collective security interests rather than isolated initiatives.
-
The Public views all of these actors - researchers, industry, government, and law enforcement - as jointly responsible for protecting their data, privacy, and the continuity of essential services. From this perspective, citizens expect every agent to operate under a clear, transparent, and accountable framework for the use of offensive countermeasures.
Now that we’ve mapped the key perspectives, we can move on to a POSIWID Analysis - examining what the current system is actually doing (Purpose Of a System Is What It Does), envisioning what a future system should achieve, and identifying the high-level initiatives required to bring that future system into reality.
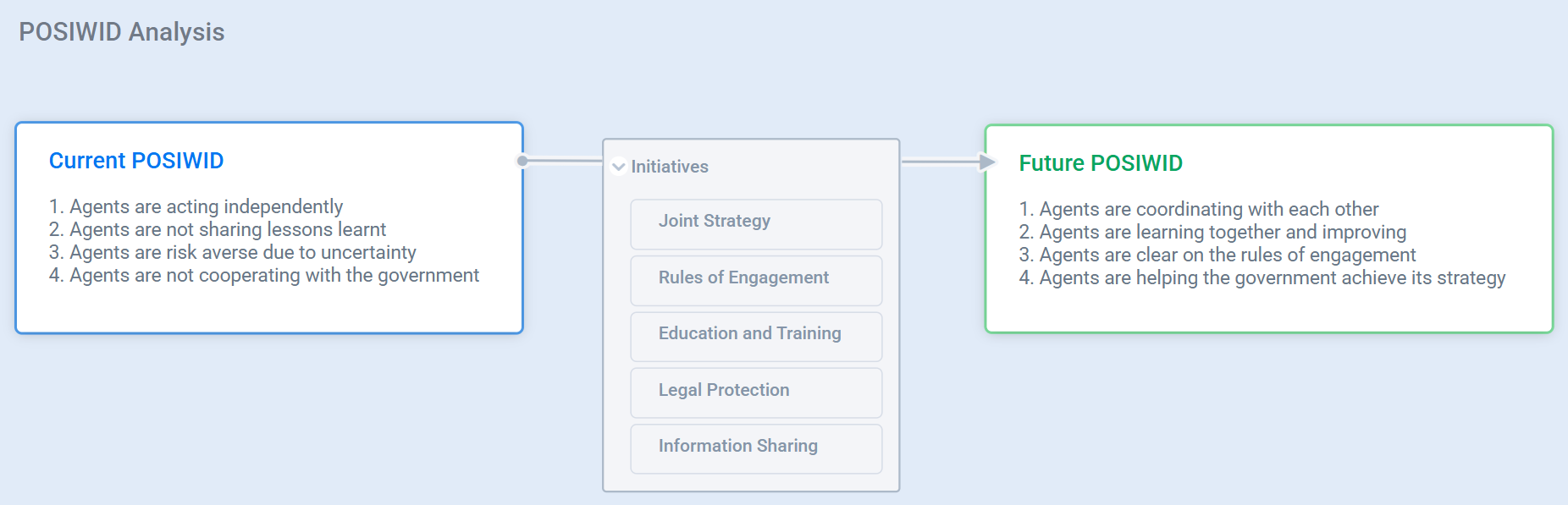
The purpose of this post was simply to capture and share my current mental model in case some of these ideas prove useful to others. As I mentioned earlier, I haven’t had the opportunity to conduct in-depth research on developments in this area since 2016, so I encourage anyone interested in the topic to explore more recent literature, frameworks and mental models.
If you know of any strong papers or models on Offensive Countermeasures or related areas, please share them with me - I’d be keen to read and learn from them.